Post by: Netwörkheäd on May 22, 2023, 06:01:50 PM
Summary
Note: This joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These #StopRansomware advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware. Visit stopransomware.gov to see all #StopRansomware advisories and learn more about other ransomware threats and no-cost resources.
The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Cyber Security Centre (ACSC) are releasing this joint Cybersecurity Advisory to disseminate known BianLian ransomware and data extortion group IOCs and TTPs identified through FBI and ACSC investigations as of March 2023.
Actions to take today to mitigate cyber threats from BianLian ransomware and data extortion: |
BianLian is a ransomware developer, deployer, and data extortion cybercriminal group that has targeted organizations in multiple U.S. critical infrastructure sectors since June 2022. They have also targeted Australian critical infrastructure sectors in addition to professional services and property development. The group gains access to victim systems through valid Remote Desktop Protocol (RDP) credentials, uses open-source tools and command-line scripting for discovery and credential harvesting, and exfiltrates victim data via File Transfer Protocol (FTP), Rclone, or Mega. BianLian group actors then extort money by threatening to release data if payment is not made. BianLian group originally employed a double-extortion model in which they encrypted victims' systems after exfiltrating the data; however, around January 2023, they shifted to primarily exfiltration-based extortion.
FBI, CISA, and ACSC encourage critical infrastructure organizations and small- and medium-sized organizations to implement the recommendations in the Mitigations section of this advisory to reduce the likelihood and impact of BianLian and other ransomware incidents.
Download the PDF version of this report (710kb):
For a downloadable copy of IOCs (35kb), see:
For a downloadable copy of IOCs in JSON format, see AA23-136A.stix.json
Technical Details
Note: This advisory uses the MITRE ATT&CK® for Enterprise framework, version 13. See the MITRE ATT&CK® Tactics and Techniques section for a table of the threat actors' activity mapped to MITRE ATT&CK® Tactics and Techniques. For assistance with mapping malicious cyber activity to the MITRE ATT&CK framework, see CISA and MITRE ATT&CK's Best Practices for MITRE ATT&CK Mapping and CISA's Decider Tool.
BianLian is a ransomware developer, deployer, and data extortion cybercriminal group. FBI observed BianLian group targeting organizations in multiple U.S. critical infrastructure sectors since June 2022. In Australia, ACSC has observed BianLian group predominately targeting private enterprises, including one critical infrastructure organization. BianLian group originally employed a double-extortion model in which they exfiltrated financial, client, business, technical, and personal files for leverage and encrypted victims' systems. In 2023, FBI observed BianLian shift to primarily exfiltration-based extortion with victims' systems left intact, and ACSC observed BianLian shift exclusively to exfiltration-based extortion. BianLian actors warn of financial, business, and legal ramifications if payment is not made.
Initial Access
BianLian group actors gain initial access to networks by leveraging compromised Remote Desktop Protocol (RDP) credentials likely acquired from initial access brokers [T1078],[T1133] or via phishing [T1566].
Command and Control
BianLian group actors implant a custom backdoor specific to each victim written in Go (see the Indicators of Compromise Section for an example) [T1587.001] and install remote management and access software—e.g., TeamViewer, Atera Agent, SplashTop, AnyDesk—for persistence and command and control [T1105],[T1219].
FBI also observed BianLian group actors create and/or activate local administrator accounts [T1136.001] and change those account passwords [T1098].
Defense Evasion
BianLian group actors use PowerShell [T1059.001] and Windows Command Shell [T1059.003] to disable antivirus tools [T1562.001], specifically Windows defender and Anti-Malware Scan Interface (AMSI). BianLian actors modify the Windows Registry [T1112] to disable tamper protection for Sophos SAVEnabled, SEDEenabled, and SAVService services, which enables them to uninstall these services. See Appendix: Windows PowerShell and Command Shell Activity for additional information, including specific commands they have used.
Discovery
BianLian group actors use a combination of compiled tools, which they first download to the victim environment, to learn about the victim's environment. BianLian group actors have used:
- Advanced Port Scanner, a network scanner used to find open ports on network computers and retrieve versions of programs running on the detected ports [T1046].
- SoftPerfect Network Scanner (netscan.exe), a network scanner that can ping computers, scan ports, and discover shared folders [T1135].
- SharpShares to enumerate accessible network shares in a domain.
- PingCastle to enumerate Active Directory (AD) [T1482]. PingCastle provides an AD map to visualize the hierarchy of trust relationships.
BianLian actors also use native Windows tools and Windows Command Shell to:
- Query currently logged-in users [T1033].
- Query the domain controller to identify:
- All groups [T1069.002].
- Accounts in the Domain Admins and Domain Computers groups [1087.002].
- All users in the domain.
- Retrieve a list of all domain controllers and domain trusts.
- Identify accessible devices on the network [T1018].
See Appendix: Windows PowerShell and Command Shell Activity for additional information, including specific commands they have used.
Credential Access
BianLian group uses valid accounts for lateral movement through the network and to pursue other follow-on activity. To obtain the credentials, BianLian group actors use Windows Command Shell to find unsecured credentials on the local machine [T1552.001]. FBI also observed BianLian harvest credentials from the Local Security Authority Subsystem Service (LSASS) memory [T1003.001], download RDP Recognizer (a tool that could be used to brute force RDP passwords or check for RDP vulnerabilities) to the victim system, and attempt to access an Active Directory domain database (NTDS.dit) [T1003.003].
In one case, FBI observed BianLian actors use a portable executable version of an Impacket tool (secretsdump.py) to move laterally to a domain controller and harvest credential hashes from it. Note: Impacket is a Python toolkit for programmatically constructing and manipulating network protocols. Through the Command Shell, an Impacket user with credentials can run commands on a remote device using the Windows management protocols required to support an enterprise network. Threat actors can run portable executable files on victim systems using local user rights, assuming the executable is not blocked by an application allowlist or antivirus solution.
See Appendix: Windows PowerShell and Command Shell Activity for additional information.
Persistence and Lateral Movement
BianLian group actors use PsExec and RDP with valid accounts for lateral movement [T1021.001]. Prior to using RDP, BianLian actors used Command Shell and native Windows tools to add user accounts to the local Remote Desktop Users group, modified the added account's password, and modified Windows firewall rules to allow incoming RDP traffic [T1562.004]. See Appendix: Windows PowerShell and Command Shell Activity for additional information.
In one case, FBI found a forensic artifact (exp.exe) on a compromised system that likely exploits the Netlogon vulnerability (CVE-2020-1472) and connects to a domain controller.
Collection
FBI observed BianLian group actors using malware (system.exe) that enumerates registry [T1012] and files [T1083] and copies clipboard data from users [T1115].
Exfiltration and Impact
BianLian group actors search for sensitive files using PowerShell scripts (See Appendix: Windows PowerShell and Command Shell Activity) and exfiltrate them for data extortion. Prior to January 2023, BianLian actors encrypted files [T1486] after exfiltration for double extortion.
BianLian group uses File Transfer Protocol (FTP) [T1048] and Rclone, a tool used to sync files to cloud storage, to exfiltrate data [T1537]. FBI observed BianLian group actors install Rclone and other files in generic and typically unchecked folders such as programdata\vmware and music folders. ACSC observed BianLian group actors use Mega file-sharing service to exfiltrate victim data [T1567.002].
BianLian's encryptor (encryptor.exe) modified all encrypted files to have the .bianlian extension. The encryptor created a ransom note, Look at this instruction.txt, in each affected directory (see Figure 1 for an example ransom note.) According to the ransom note, BianLian group specifically looked for, encrypted, and exfiltrated financial, client, business, technical, and personal files.
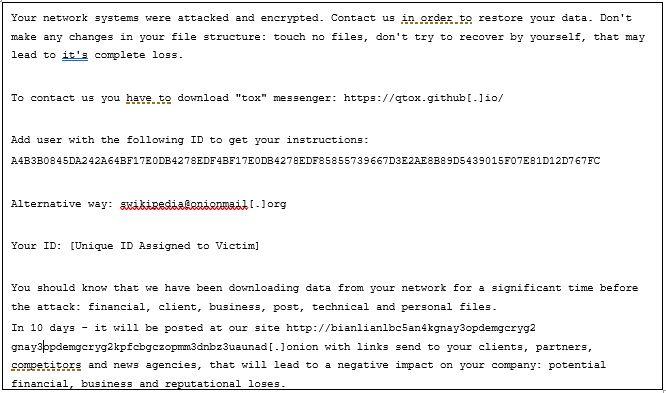 |
If a victim refuses to pay the ransom demand, BianLian group threatens to publish exfiltrated data to a leak site maintained on the Tor network. The ransom note provides the Tox ID A4B3B0845DA242A64BF17E0DB4278EDF85855739667D3E2AE8B89D5439015F07E81D12D767FC, which does not vary across victims. The Tox ID directs the victim organization to a Tox chat via https://qtox.github[.]io and includes an alternative contact email address (swikipedia@onionmail[.]org or xxx@mail2tor[.]com). The email address is also the same address listed on the group's Tor site under the contact information section. Each victim company is assigned a unique identifier included in the ransom note. BianLian group receives payments in unique cryptocurrency wallets for each victim company.
BianLian group engages in additional techniques to pressure the victim into paying the ransom; for example, printing the ransom note to printers on the compromised network. Employees of victim companies also reported receiving threatening telephone calls from individuals associated with BianLian group.
Indicators of Compromise (IOC)
See Table 1 for IOCs obtained from FBI investigations as of March 2023.
Name | SHA-256 Hash | Description |
7b15f570a23a5c5ce8ff942da60834a9d0549ea3ea9f34f900a09331325df893 | Malware associated with BianLian intrusions, which is an example of a possible backdoor developed by BianLian group. | |
1fd07b8d1728e416f897bef4f1471126f9b18ef108eb952f4b75050da22e8e43 | Example of a BianLian encryptor. | |
0c1eb11de3a533689267ba075e49d93d55308525c04d6aff0d2c54d1f52f5500 | Possible NetLogon vulnerability (CVE-2020-1472) exploitation. | |
40126ae71b857dd22db39611c25d3d5dd0e60316b72830e930fba9baf23973ce | Enumerates registry and files. Reads clipboard data. |
MITRE ATT&CK Techniques
See Table 2 for all referenced threat actor tactics and techniques in this advisory.
Technique Title | ID | Use |
|---|---|---|
Resource Development | ||
Develop Capabilities: Malware | BianLian group actors developed a custom backdoor used in their intrusions. | |
Initial Access | ||
External Remote Services | BianLian group actors used RDP with valid accounts as a means of gaining initial access and for lateral movement. | |
Phishing | BianLian group actors used phishing to obtain valid user credentials for initial access. | |
Valid Accounts | BianLian group actors used RDP with valid accounts as a means of gaining initial access and for lateral movement. | |
Execution | ||
Command and Scripting Interpreter: PowerShell | BianLian group actors used PowerShell to disable AMSI on Windows. See Appendix: Windows PowerShell and Command Shell Activity for additional information. | |
Command and Scripting Interpreter: Windows Command Shell | BianLian group actors used Windows Command Shell to disable antivirus tools, for discovery, and to execute their tools on victim networks. See Appendix: Windows PowerShell and Command Shell Activity for additional information. | |
Scheduled Task/Job: Scheduled Task | BianLian group actors used a Scheduled Task run as SYSTEM (the highest privilege Windows accounts) to execute a Dynamic Link Library (DLL) file daily. See Appendix: Windows PowerShell and Command Shell Activity for additional information. | |
Persistence | ||
Account Manipulation | BianLian group actors changed the password of an account they created. BianLian actors modified the password of an account they added to the local Remote Desktop Users group. | |
Create Account: Local Account | BianLian group actors created/activated a local administrator account. BianLian group actors used net.exe to add a user account to the local Remote Desktop Users group. (See Appendix: Windows PowerShell and Command Shell Activity for more information.) | |
Defense Evasion | ||
Modify Registry | BianLian group actors modified the registry to disable user authentication for RDP connections, allow a user to receive help from Remote Assistance, and disable tamper protection for Sophos SAVEnabled, SEDEenabled, and SAVService services, which enables them to uninstall these services. | |
Impair Defenses: Disable or Modify Tools | BianLian group actors disabled Windows defender, AMSI, and Sophos SAVEnabled and SEDEenabled tamper protection services. See Appendix: Windows PowerShell and Command Shell Activity for additional information. | |
Impair Defenses: Disable or Modify System Firewall | BianLian group actors added modified firewalls to allow RDP traffic by adding new rules to the Windows firewall that allow incoming RDP traffic and enable a pre-existing Windows firewall rule group named Remote Desktop. | |
Credential Access | ||
OS Credential Dumping: LSASS Memory | BianLian group actors accessed credential material stored in the process memory of the LSASS. See Appendix: Windows PowerShell and Command Shell Activity for additional information. | |
OS Credential Dumping: NTDS | BianLian group actors attempted to access or create a copy of the Active Directory domain database in order to steal credential information and to obtain other information about domain members such as devices, users, and access rights. | |
Unsecured Credentials: Credentials In Files | BianLian group actors searched local file systems and remote file shares for files containing insecurely stored credentials. | |
Discovery | ||
Account Discovery: Domain Account | BianLian group actors queried the domain controller to identify accounts in the Domain Admins and Domain Computers groups. This information can help adversaries determine which domain accounts exist to aid in follow-on activity. | |
Domain Trust Discovery | BianLian group actors used PingCastle to enumerate the AD and map trust relationships. BianLian group actors retrieved a list of domain trust relationships used to identify lateral movement opportunities in Windows multi-domain/forest environments. | |
File and Directory Discovery | BianLian group used malware (system.exe) that enumerates files. | |
Network Service Discovery | BianLian actors used Advanced Port Scanner and SoftPerfect Network Scanner to ping computers, scan ports, and identify program versions running on ports. | |
Network Share Discovery | BianLian actors used SoftPerfect Network Scanner, which can discover shared folders. BianLian group actors used SharpShares to enumerate accessible network shares in a domain. | |
Permission Groups Discovery: Domain Groups | BianLian group actors queried the domain controller to identify groups. | |
Query Registry | BianLian group used malware (system.exe) that enumerates registry. | |
Remote System Discovery | BianLian group actors attempted to get a listing of other systems by IP address, hostname, or other logical identifier on a network that may be used for lateral movement. BianLian group actors retrieved a list of domain controllers. | |
System Owner User Discovery | BianLian group actors queried currently logged-in users on a machine. | |
Lateral Movement | ||
Remote Services: Remote Desktop Protocol | BianLian group actors used RDP with valid accounts for lateral movement. | |
Collection | ||
Clipboard Data | BianLian group actors' malware collects data stored in the clipboard from users copying information within or between applications. | |
Command and Control | ||
Ingress Tool Transfer | BianLian group actors transferred tools or other files from an external system into a compromised environment. | |
Remote Access Software | BianLian group actors used legitimate desktop support and remote access software, such as TeamViewer, Atera, and SplashTop, to establish an interactive command and control channel to target systems within networks. | |
Exfiltration | ||
Transfer Data to Cloud Account | BianLian group actors used Rclone to exfiltrate data to a cloud account they control on the same service to avoid typical file transfers/downloads and network-based exfiltration detection. | |
Exfiltration Over Alternative Protocol | BianLian group actors exfiltrated data via FTP. | |
Exfiltration Over Web Service: Exfiltration to Cloud Storage | BianLian group actors exfiltrated data via Mega public file-sharing service. | |
Impact | ||
Data Encrypted for Impact | BianLian group actors encrypted data on target systems. |
Mitigations
FBI, CISA, and ACSC recommend organizations implement the mitigations below to improve your organization's cybersecurity posture on the basis of the threat actors' activity. These mitigations align with the Cross-Sector Cybersecurity Performance Goals (CPGs) developed by CISA and the National Institute of Standards and Technology (NIST). The CPGs provide a minimum set of practices and protections that CISA and NIST recommend all organizations implement. CISA and NIST based the CPGs on existing cybersecurity frameworks and guidance to protect against the most common and impactful threats and TTPs. Visit CISA's Cross-Sector Cybersecurity Performance Goals for more information on the CPGs, including additional recommended baseline protections.
- Reduce threat of malicious actors using remote access tools by:
- Auditing remote access tools on your network to identify currently used and/or authorized software.
- Reviewing logs for execution of remote access software to detect abnormal use of programs running as a portable executable [CPG 2.T].
- Using security software to detect instances of remote access software only being loaded in memory.
- Requiring authorized remote access solutions only be used from within your network over approved remote access solutions, such as virtual private networks (VPNs) or virtual desktop interfaces (VDIs).
- Blocking both inbound and outbound connections on common remote access software ports and protocols at the network perimeter.
- Implement application controls to manage and control execution of software, including allowlisting remote access programs.
- Application controls should prevent installation and execution of portable versions of unauthorized remote access and other software. A properly configured application allowlisting solution will block any unlisted application execution. Allowlisting is important because antivirus solutions may fail to detect the execution of malicious portable executables when the files use any combination of compression, encryption, or obfuscation.
See NSA Cybersecurity Information sheet Enforce Signed Software Execution Policies for additional guidance.
- Strictly limit the use of RDP and other remote desktop services. If RDP is necessary, rigorously apply best practices, for example [CPG 2.W]:
- Audit the network for systems using RDP.
- Close unused RDP ports.
- Enforce account lockouts after a specified number of attempts.
- Apply phishing-resistant multifactor authentication (MFA).
- Log RDP login attempts.
- Disable command-line and scripting activities and permissions [CPG 2.N].
- Restrict the use of PowerShell, using Group Policy, and only grant to specific users on a case-by-case basis. Typically, only those users or administrators who manage the network or Windows operating systems (OSs) should be permitted to use PowerShell [CPG 2.E].
- Update Windows PowerShell or PowerShell Core to the latest version and uninstall all earlier PowerShell versions. Logs from Windows PowerShell prior to version 5.0 are either non-existent or do not record enough detail to aid in enterprise monitoring and incident response activities [CPG 1.E, 2.S, 2.T].
- Enable enhanced PowerShell logging [CPG 2.T, 2.U].
- PowerShell logs contain valuable data, including historical OS and registry interaction and possible TTPs of a threat actor's PowerShell use.
- Ensure PowerShell instances, using the latest version, have module, script block, and transcription logging enabled (enhanced logging).
- The two logs that record PowerShell activity are the PowerShell Windows Event Log and the PowerShell Operational Log. FBI and CISA recommend turning on these two Windows Event Logs with a retention period of at least 180 days. These logs should be checked on a regular basis to confirm whether the log data has been deleted or logging has been turned off. Set the storage size permitted for both logs to as large as possible.
- Configure the Windows Registry to require User Account Control (UAC) approval for any PsExec operations requiring administrator privileges to reduce the risk of lateral movement by PsExec.
- Review domain controllers, servers, workstations, and active directories for new and/or unrecognized accounts [CPG 4.C].
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege [CPG 2.E].
- Reduce the threat of credential compromise via the following:
- Place domain admin accounts in the protected users' group to prevent caching of password hashes locally.
- Implement Credential Guard for Windows 10 and Server 2016 (Refer to Microsoft: Manage Windows Defender Credential Guard for more information). For Windows Server 2012R2, enable Protected Process Light for Local Security Authority (LSA).
- Refrain from storing plaintext credentials in scripts.
- Implement time-based access for accounts set at the admin level and higher [CPG 2.A, 2.E]. For example, the Just-in-Time (JIT) access method provisions privileged access when needed and can support enforcement of the principle of least privilege (as well as the Zero Trust model). This is a process where a network-wide policy is set in place to automatically disable admin accounts at the Active Directory (AD) level when the account is not in direct need. Individual users may submit their requests through an automated process that grants them access to a specified system for a set timeframe when they need to support the completion of a certain task.
In addition, FBI, CISA, and ACSC recommend network defenders apply the following mitigations to limit potential adversarial use of common system and network discovery techniques and to reduce the impact and risk of compromise by ransomware or data extortion actors:
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (e.g., hard drive, storage device, or the cloud).
- Maintain offline backups of data, and regularly maintain backup and restoration (daily or weekly at minimum). By instituting this practice, an organization minimizes the impact of disruption to business practices as they will not be as severe and/or only have irretrievable data [CPG 2.R]. ACSC recommends organizations follow the 3-2-1 backup strategy in which organizations have three copies of data (one copy of production data and two backup copies) on two different media such as disk and tape, with one copy kept off-site for disaster recovery.
- Require all accounts with password logins (e.g., service account, admin accounts, and domain admin accounts) to comply with National Institute for Standards and Technology (NIST) standards for developing and managing password policies.
- Use longer passwords consisting of at least 15 characters [CPG 2.B].
- Store passwords in hashed format using industry-recognized password managers.
- Add password user "salts" to shared login credentials.
- Avoid reusing passwords [CPG 2.C].
- Implement multiple failed login attempt account lockouts [CPG 2.G].
- Disable password "hints".
- Refrain from requiring password changes more frequently than once per year.
Note: NIST guidance suggests favoring longer passwords instead of requiring regular and frequent password resets. Frequent password resets are more likely to result in users developing password "patterns" cyber criminals can easily decipher. - Require administrator credentials to install software.
- Require phishing-resistant multifactor authentication for all services to the extent possible, particularly for webmail, virtual private networks, and accounts that access critical systems [CPG 2.H].
- Keep all operating systems, software, and firmware up to date. Timely patching is one of the most efficient and cost-effective steps an organization can take to minimize its exposure to cybersecurity threats. Organizations should patch vulnerable software and hardware systems within 24 to 48 hours from vulnerability disclosure. Prioritize patching known exploited vulnerabilities in internet-facing systems [CPG 1.E].
- Segment networks to prevent the spread of ransomware. Network segmentation can help prevent the spread of ransomware by controlling traffic flows between—and access to—various subnetworks, restricting further lateral movement [CPG 2.F].
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool. To aid in detecting ransomware, implement a tool that logs and reports all network traffic, including lateral movement activity on a network. Endpoint detection and response (EDR) tools are particularly useful for detecting lateral connections, as they have insight into common and uncommon network connections for each host [CPG 3.A].
- Install, regularly update, and enable real time detection for antivirus software on all hosts.
- Disable unused ports [CPG 2.V].
- Consider adding an email banner to emails received from outside your organization [CPG 2.M].
- Ensure all backup data is encrypted, immutable (i.e., cannot be altered or deleted), and covers the entire organization's data infrastructure [CPG 2.K, 2.L, 2.R].
Validate Security Controls
In addition to applying mitigations, FBI, CISA, and ACSC recommend exercising, testing, and validating your organization's security program against the threat behaviors mapped to the MITRE ATT&CK for Enterprise framework in this advisory. FBI, CISA, and ACSC recommend testing your existing security controls inventory to assess how they perform against the ATT&CK techniques described in this advisory.
To get started:
- Select an ATT&CK technique described in this advisory (see Table 2).
- Align your security technologies against the technique.
- Test your technologies against the technique.
- Analyze your detection and prevention technologies' performance.
- Repeat the process for all security technologies to obtain a set of comprehensive performance data.
- Tune your security program, including people, processes, and technologies, based on the data generated by this process.
FBI, CISA, and ACSC recommend continually testing your security program, at scale, in a production environment to ensure optimal performance against the MITRE ATT&CK techniques identified in this advisory.
RESOURCES
- Stopransomware.gov, a whole-of-government approach with one central location for U.S. ransomware resources and alerts.
- cyber.gov.au for the Australian Government's central location to report cyber incidents, including ransomware, and to see advice and alerts. The site also provides ransomware advisories for businesses and organizations to help mitigate cyber threats.
- CISA-Multi-State Information Sharing and Analysis Center (MS-ISAC) Joint Ransomware Guide for guidance on mitigating and responding to a ransomware attack
- For no-cost cyber hygiene services for U.S. organizations, Cyber Hygiene Services and Ransomware Readiness Assessment.
Reporting
The FBI is seeking any information that can be shared, including boundary logs showing communication to and from foreign IP addresses, a sample ransom note, communications with BianLian actors, Bitcoin wallet information, decryptor files, and/or a benign sample of an encrypted file. The FBI and CISA do not encourage paying ransom, as payment does not guarantee victim files will be recovered. Furthermore, payment may also embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and/or fund illicit activities. Regardless of whether you or your organization have decided to pay the ransom, the FBI and CISA urge you to promptly report ransomware incidents to a local FBI Field Office or CISA at cisa.gov/report. Australian organizations that have been impacted or require assistance in regard to a ransomware incident can contact ACSC via 1300 CYBER1 (1300 292 371) or by submitting a report cyber.gov.au.
Acknowledgements
Microsoft and Sophos contributed to this advisory.
APPENDIX: WINDOWS PowerSHell and COMMAND SHELL ACTIVITY
Through FBI investigations as of March 2023, FBI has observed BianLian actors use the commands in Table 3. ACSC has observed BianLian actors use some of the same commands.
Command | Use |
[Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed','NonPublic,* Static').SetValue($null,$true) | Disables the AMSI on Windows. AMSI is a built-in feature on Windows 10 and newer that provides an interface for anti-malware scanners to inspect scripts prior to execution. When AMSI is disabled, malicious scripts may bypass antivirus solutions and execute undetected. |
cmd.exe /Q /c for /f "tokens=1,2 delims= " ^%A in ('"tasklist /fi "Imagename eq lsass.exe" | find "lsass""') do rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump ^%B \Windows\Temp\ | Creates a memory dump lsass.exe process and saves it as a CSV filehttps://attack.mitre.org/versions/v12/techniques/T1003/001/. BianLian actors used it to harvest credentials from lsass.exe. |
cmd.exe /Q /c net user | Activates the local Administrator account. |
cmd.exe /Q /c net user " | Changes the password of the newly activated local Administrator account. |
cmd.exe /Q /c quser 1> \\127.0.0.1\C$\Windows\Temp\ | Executes quser.exe to query the currently logged-in users on a machine. The command is provided arguments to run quietly and exit upon completion, and the output is directed to the \Windows\Temp directory. |
dism.exe /online /Disable-Feature /FeatureName:Windows-Defender /Remove /NoRestart | Using the Deployment Image Servicing and Management (DISM) executable file, removes the Windows Defender feature. |
dump.exe -no-pass -just-dc user.local/ | Executes secretsdump.py, a Portable Executable version of an Impacket tool. Used to dump password hashes from domain controllers. |
exp.exe -n | Possibly attempted exploitation of the NetLogon vulnerability (CVE-2020-1472). |
findstr /spin "password" *.* >C:\Users\training\Music\ | Searches for the string password in all files in the current directory and its subdirectories and puts the output to a file. |
ldap.exe -u user\ | Connects to the organization's Lightweight Directory Access Protocol (LDAP) server. |
logoff | Logs off the current user from a Windows session. Can be used to log off multiple users at once. |
mstsc | Launches Microsoft Remote Desktop Connection client application in Windows. |
net group /domain | Retrieves a list of all groups from the domain controller. |
net group 'Domain Admins' /domain | Queries the domain controller to retrieve a list of all accounts from Domain Admins group. |
net group 'Domain Computers' /domain | Queries the domain controller to retrieve a list of all accounts from Domain Computers group. |
net user /domain | Queries the domain controller to retrieve a list of all users in the domain. |
net.exe localgroup "Remote Desktop Users" | Adds a user account to the local Remote Desktop Users group. |
net.exe user | Modifies the password for the specified account. |
netsh.exe advfirewall firewall add rule "name=allow RemoteDesktop" dir=in * protocol=TCP localport= | Adds a new rule to the Windows firewall that allows incoming RDP traffic. |
netsh.exe advfirewall firewall set rule "group=remote desktop" new enable=Yes | Enables the pre-existing Windows firewall rule group named Remote Desktop. This rule group allows incoming RDP traffic. |
nltest /dclist | Retrieves a list of domain controllers. |
nltest /domain_trusts | Retrieves a list of domain trusts. |
ping.exe -4 -n 1 * | Sends a single ICMP echo request packet to all devices on the local network using the IPv4 protocol. The output of the command will show if the device is reachable or not. |
quser; ([adsisearcher]"(ObjectClass=computer)").FindAll().count;([adsisearcher]"(ObjectClass=user)").FindAll().count;[Security.Principal.WindowsIdentity]::GetCurrent() | select name;net user "$env:USERNAME" /domain; (Get-WmiObject -class Win32_OperatingSystem).Caption; Get-WmiObject -Namespace root\cimv2 -Class Win32_ComputerSystem; net group "domain admins" /domain; nltest /dclist:; nltest /DOMAIN_TRUSTS | Lists the current Windows identity for the logged-in user and displays the user's name. Uses the Active Directory Services Interface (ADSI) to search for all computer and user objects in the domain and returns counts of the quantities found. Lists information about the current user account from the domain, such as the user's name, description, and group memberships. Lists information about the operating system installed on the local computer. Lists information about the "Domain Admins" group from the domain. Lists all domain controllers in the domain. Displays information about domain trusts. |
reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal * Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD /d 0 /f | Adds/overwrites a new Registry value to disable user authentication for RDP connections. |
reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /* v fAllowToGetHelp /t REG_DWORD /d 1 /f | Adds/overwrites a new Registry value to allow a user to receive help from Remote Assistance. |
reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sophos Endpoint * Defense\TamperProtection\Config" /t REG_DWORD /v SAVEnabled /d 0 /f | Adds/overwrites a new Registry value to disable tamper protection for Sophos antivirus named SAVEnabled. |
reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sophos Endpoint * Defense\TamperProtection\Config" /t REG_DWORD /v SEDEnabled /d 0 /f | Adds/overwrites a new Registry value to disable tamper protection for Sophos antivirus named SEDEnabled. |
reg.exe ADD * HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Sophos\SAVService\TamperProtection /t REG_DWORD /v Enabled /d 0 /f | Adds/overwrites a new registry value to disable tamper protection for a Sophos antivirus service called SAVService. |
reg.exe copy hklm\system\CurrentControlSet\services\tvnserver * hklm\system\CurrentControlSet\control\safeboot\network\tvnserver /s /f | Copies the configuration settings for the tvnserver service to a new location in the registry that will be used when the computer boots into Safe Mode with Networking. This allows the service to run with the same settings in Safe Mode as it does in normal mode. |
s.exe /threads:50 /ldap:all /verbose /outfile:c:\users\ | Executes SharpShares. |
schtasks.exe /RU SYSTEM /create /sc ONCE / | Creates a Scheduled Task run as SYSTEM at 0443 AM. When the task is run, cmd.exe uses crundll32.exe to run the DLL file netsh.dll. (It is likely that netsh.dll is a malware file and not associated with netsh.) |
start-process PowerShell.exe -arg C:\Users\Public\Music\ | Executes a PowerShell script, while keeping the PowerShell window hidden from the user. |
Disclaimer
The information in this report is being provided "as is" for informational purposes only. FBI, CISA, and ACSC do not endorse any commercial product or service, including any subjects of analysis. Any reference to specific commercial products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply endorsement, recommendation, or favoring by FBI, CISA, or ACSC.
Source: #StopRansomware: BianLian Ransomware Group (https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-136a)