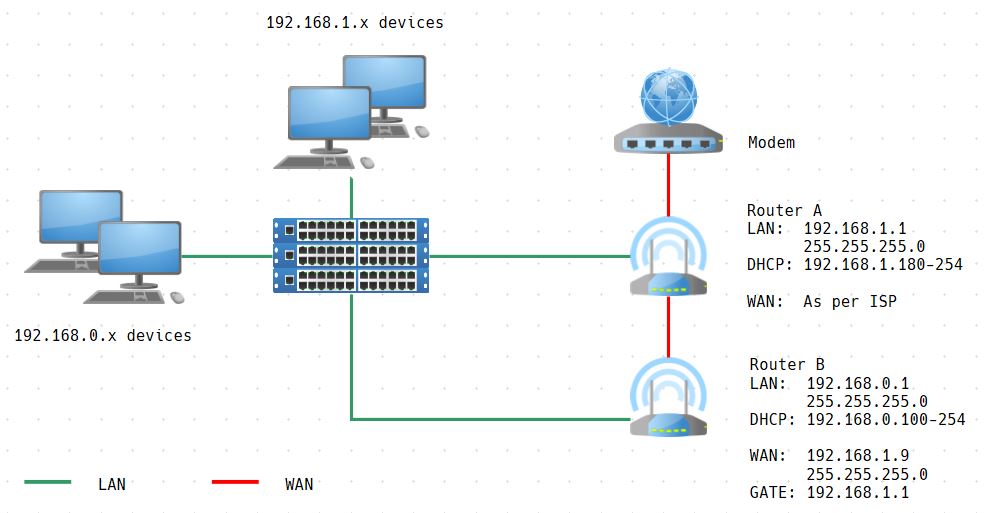
Quote from: deanwebb on February 03, 2022, 11:19:27 AMPalo Alto is what our customer uses. Of course, they are a multi-million dollar company and we are a small business. Hence the reason I have to make do with what we have, and with my skill level.
The *best* device for handling filters like this is a commercial-grade firewall. Palo Alto, Fortinet are my two recommended vendors. But this does illustrate the limitations of consumer-grade / small-business-grade gear. They'll only do so many things. If you require more finesse or robustness, then a higher-price commercial-grade device is on order. But, if this is in an operational technology environment, it may be all you have to work with, so we better make it work, eh?

QuoteBack to the question: Outbound, the source is the control. Destination is "any" - either the word or a wildcard IP address entry like 0.0.0.0 or *.*.*.*, whatever the vendor permits. Inbound, it's any -> control. If we use only the router IP address, then traffic not originating from the router will play through.
So something like the attached should block all ports for 192.168.1.123 except for 80 and 443, correct? I know it's clunky using a blacklist for this and I'd love to use a whitelist but that would mess up the other uses of the router.